Digital Security Tips for Researchers
In this age of widespread surveillance, it’s important to keep your research safe and secure from the prying eyes of governments and corporations. While most digital security tools are available for free, they do require a change in your digital habits. Good security will require a trade-off: the techniques that keep you safest are often less convenient than their non-secure alternatives that you are accustomed to. Consider participating in a threat modeling exercise or attending a CryptoParty
1) Take the time to master some essential personal security practices
These are the backbone of good digital security. They are a must for anyone, even those not conducting sensitive research.
- Use good passwords, two-factor authentication when available, and preferably use a password manager.
- Encrypt your phones & laptops using full-disc encryption. In the event that your device is seized or stolen, this will protect the data on your hard-drive. You can do this for almost all devices including macs, PCs, and androids. Recent iPhones are already setup with full-disc encryption, but you can find more information about securing your iPhone here.
- Update your software and operating system regularly. Security vulnerabilities are being fixed all the time.
2) Surf the web safer while researching
Most research these days is done through an internet browser, and there’s a lot you can do you improve the safety of your browsing.
- Avoid trackers and make your traffic more secure via chrome or firefox plugins: Privacy Badger and HTTPS-everywhere
- Concerned about the surveillance capabilities of your internet service provider? consider using a VPN or Tor while researching on the internet.
3) Communicate and share files securely
- Use encrypted chat programs such as signal, wire, or Off-the-record as an alternative to email.
- If you must use email (and who doesn’t?), use an alternative provider such as riseup.net, protonmail, and resist.ca
- To share files without going through google or dropbox, use OnionShare, Share.Riseup.net, or SpiderOak One
4) Learn more!
Developing good digital security practices takes time. These guides go more in depth about using these technologies. Read them and share them with your fellow researchers:
- EFF’s Surveillance Self-Defense
- Security in a box
- Riseup.net’s Security Guide
- DIY Guide to Feminist Cybersecurity
- My Shadow: Take control of your data
- Equality Labs – South Asian Women/Gender Non-Conforming/Trans Technology Startup
- Centre for Investigative Journalism – Information Security for Journalists
- Holistic Security Manual
- Library Freedom Project
Other Tools and Research Guides
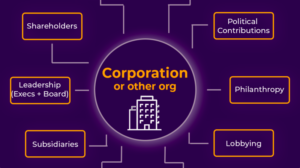
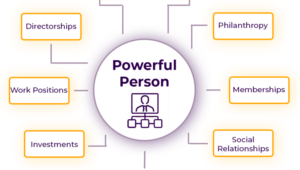
- LittleSis.org, an involuntary facebook of the 1% that aggregates power research info all in one place
- MuckRock, a tool for submitting Freedom of Information Act requests
- DocumentCloud, a great resource for finding, sharing, and analyzing large documents and finding Freedom of Information Act requests received by other researchers
- Dirt Diggers Digest Guide to Strategic Corporate Research
- Alliance for a Just Society’s Guide to Money in Politics
- Professor William Domhoff’s How to Do Power Structure Research